In a new report, leading cybersecurity company McAfee has found that the surge in cryptomining malware growth that began in Q4 2017 continued through the first half of 2018.
McAfee has released its “McAfee Labs Threats Report: September 2018” in which it has examined the growth and trends of new cyber threats in Q2 2018.
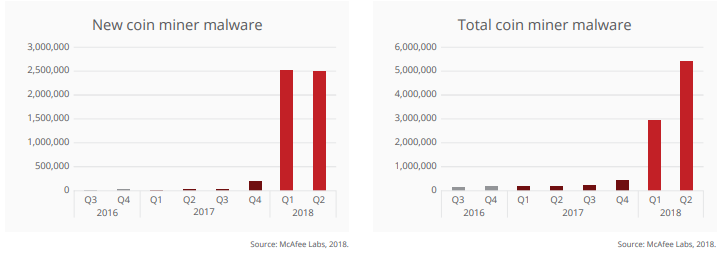
According to the report, cryptomining malware has quickly emerged as a factor on the threat landscape – new cryptomining malware samples grew a stunning 629% to more than 2.9 million samples in Q1 2018 compared to around 400k in Q4 2017. This trend continued in Q2 2018 as total samples grew by 86% with more than 2.5 million new samples. McAfee Labs said that older malware, such as ransomware, are being newly retooled with mining capabilities.
The report also pointed out that cryptomining is targeting specific groups in some cases rather than a broad field of potential victims. To that end, it cited the example of a cryptomining malware strain that targeted gamers on a Russian forum by posing as a “mod” claiming to enhance popular games. Gamers were tricked into downloading the malicious software, which then used their computer resources for profit.
While cryptomining malware primarily targets PCs, other devices have become victims, it added. For instance, Android phones in China and Korea have been exploited by the ADB.Miner malware into producing Monero cryptocurrency for its perpetrators.
“A few years ago, we wouldn’t think of internet routers, video-recording devices, and other Internet of Things devices as platforms for cryptomining because their CPU speeds were too insufficient to support such productivity,” said Christiaan Beek, Lead Scientist and Senior Principal Engineer with McAfee Advanced Threat Research.
“Today, the tremendous volume of such devices online and their propensity for weak passwords present a very attractive platform for this activity. If I were a cybercriminal who owns a botnet of 100,000 such IoT devices, it would cost me next to nothing financially to produce enough cryptocurrency to create a new, profitable revenue stream.”
In addition, McAfee Advanced Threat Research identified top security threats to users and implementers of blockchain technologies. They found that phishing, malware, and implementation vulnerabilities are the primary attack vectors.

<Copyright ⓒ TokenPost, unauthorized reproduction and redistribution prohibited>

























Comment 45